With the increasing concerns over online privacy and security, more and more people are turning to VPNs to protect their data and maintain their anonymity while browsing the web. However, with the countless options available, choosing the right VPN can be a daunting task.
In this guide, we will break down the basics of VPNs, explore their importance, and discuss the key features to consider when selecting a VPN. We will also delve into the differences between free and paid VPNs, and provide tips on evaluating VPN providers. By the end of this article, you will have a clear understanding of what to look for in a VPN and be equipped to make an informed decision.
Fundamentals of VPNs

What is a VPN?
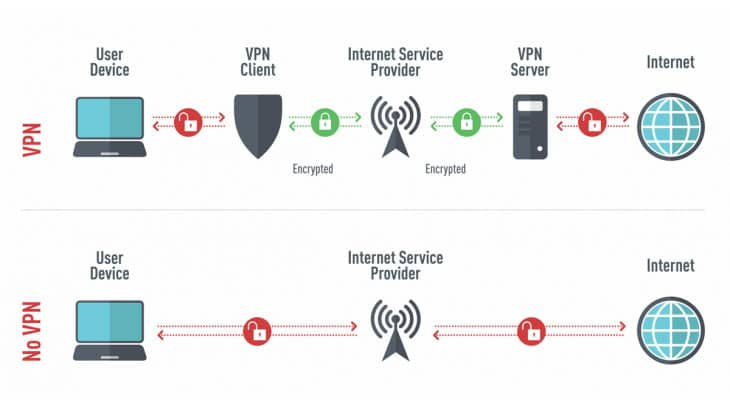
In the intricate landscape of digital communication, Virtual Private Networks (VPNs) emerge as a beacon of security and privacy. At its core, a VPN establishes a secure connection, or tunnel, between your device and virtual servers on the internet, shielding your online activities from prying eyes. By leveraging encryption techniques and routing your internet traffic through a VPN server, VPNs ensure that your browsing data remains confidential and your virtual footprint obfuscated.
A VPN functions as a conduit, encapsulating your data within a secure tunnel, thereby rendering it inaccessible to external entities, including your Internet Service Provider (ISP) and potential cyber adversaries. This clandestine layer of protection not only safeguards your sensitive information but also fortifies your online privacy, enabling you to traverse the digital realm with enhanced confidence.
How VPNs Work: Tunneling and Encryption Explained
Delving into the mechanics of VPNs unveils two pivotal processes: tunneling and encryption. Tunneling involves encapsulating your data packets within an encrypted envelope, ensuring secure transmission between your device and the VPN server. This process establishes a fortified conduit through which your internet traffic flows, shielding it from interception or tampering.
Encryption, the cornerstone of VPN technology, involves scrambling your data using sophisticated algorithms, transforming it into an unintelligible cipher. Upon reaching the VPN server, your data is decrypted and forwarded to its intended destination, fostering a seamless yet secure browsing experience. By integrating these processes, VPNs create a sanctuary of anonymity, safeguarding your online activities from surveillance and cyber threats.
VPN Protocols: PPTP, L2TP/IPsec, OpenVPN, and Others
In the realm of VPNs, protocols serve as the architectural blueprints, dictating the methodology of data transmission and encryption. Several protocols have garnered acclaim for their efficacy and robust security features:
- PPTP (Point-to-Point Tunneling Protocol): Recognized for its simplicity and compatibility, PPTP facilitates rapid data transmission but may not offer the same level of security as other protocols.
- L2TP/IPsec (Layer 2 Tunneling Protocol with IP Security): This protocol amalgamates the best of both worlds, leveraging the tunneling capabilities of L2TP and the robust encryption of IPsec, ensuring a harmonious balance between speed and security.
- OpenVPN: Renowned for its open-source nature and adaptability, OpenVPN employs cutting-edge encryption algorithms, fostering a secure and versatile VPN connection.
- Others: Additional protocols, such as SSTP and IKEv2, further augment the diverse arsenal of VPN options, catering to varied requirements and preferences.
The Role of VPN Servers in Connection Security
VPN servers serve as the linchpins of connection security, orchestrating the intricate dance of data transmission and encryption. By routing your internet traffic through a VPN server, you inherit its virtual location, thereby masking your true IP address and fostering a cloak of anonymity.
Furthermore, VPN servers operate in diverse geographic locations, enabling users to circumvent geo-restrictions and access region-locked content. Whether you seek to stream your favorite shows or bolster your online security, VPN servers play an indispensable role, facilitating secure and unrestricted access to the digital cosmos.
The Importance of Using a VPN

Using a VPN offers a myriad of benefits, ranging from enhancing online privacy to bypassing geo-restrictions. Let’s take a closer look at why using a VPN is crucial in today’s digital landscape.
Enhancing Online Privacy
In an era where our personal information is constantly at risk, maintaining our online privacy has become paramount. With cybercriminals lurking around every corner of the internet, a VPN becomes a powerful tool in safeguarding your sensitive data.
When you connect to the internet without a VPN, your online activities are exposed to prying eyes. Hackers, government agencies, and even your Internet Service Provider (ISP) can monitor your online behavior, track your browsing history, and collect your personal information. However, with a VPN, you can rest assured that your online activities remain confidential and protected.
A VPN achieves this by encrypting your internet traffic, making it unreadable to anyone who may intercept it. This encryption process involves scrambling your data into a code that can only be deciphered by the intended recipient – in this case, the VPN server you are connected to. As a result, even if someone manages to intercept your data, they won’t be able to make sense of it.
In addition to encrypting your internet traffic, a VPN also hides your IP address. Your IP address is a unique identifier that reveals your location and can be used to track your online activities. By masking your IP address with that of the VPN server, a VPN ensures that your online presence remains anonymous. This makes it difficult for anyone to trace your online activities back to you.
Bypassing Geo-Restrictions
Have you ever encountered a message saying, “This content is not available in your country”? Geo-restrictions are limitations imposed by certain websites and streaming services, restricting access based on your location. With a VPN, you can bypass these restrictions by connecting to a server in a different country.
When you connect to a VPN server located in a different country, you effectively change your virtual location. This means that websites and streaming services will see your connection as originating from the country where the VPN server is located, rather than your actual location. As a result, you can access geo-blocked content and enjoy a broader range of online resources.
For example, let’s say you are traveling abroad and want to watch your favorite TV show that is only available in your home country. Without a VPN, you would be greeted with a message stating that the content is not accessible from your current location. However, by connecting to a VPN server in your home country, you can bypass this restriction and stream the show as if you were back home.
In addition to bypassing geo-restrictions, a VPN also allows you to access region-specific content. Some websites and streaming services offer different content or pricing based on the user’s location. By connecting to a VPN server in a specific country, you can access content and services that are otherwise unavailable in your own country.
Furthermore, using a VPN can also protect you from bandwidth throttling. Internet Service Providers sometimes intentionally slow down certain types of internet traffic, such as streaming or torrenting, to manage network congestion or push users towards their own services. By encrypting your internet traffic and hiding your online activities, a VPN can help prevent your ISP from throttling your connection, ensuring a smoother and faster browsing experience.
5 Popular VPN Apps People Use: Features, Security Standards, and Safety
Navigating the intricate realm of VPN apps can be a daunting task, given the myriad number of devices and options available. To simplify your quest for online security and privacy, we delve into five popular VPN apps, elucidating their features, security standards, and safety parameters.
ProtonVPN

Features: Proton VPN stands as a paragon of privacy-centric design, offering a gamut of features tailored for discerning users. Noteworthy attributes include the Secure Core architecture, which routes user traffic through multiple servers, bolstering anonymity. Additionally, ProtonVPN incorporates split tunneling, enabling users to segregate and route specific traffic through the VPN connection, thereby optimizing performance.
Security Standard: Proton VPN exemplifies excellence in security, employing robust encryption protocols and adhering to a stringent no-logs policy. The incorporation of advanced encryption algorithms ensures data integrity, while the no-logs policy fosters a clandestine environment devoid of digital footprints.
Safety: In terms of safety, ProtonVPN’s commitment to privacy is unwavering, with features such as a kill switch and DNS leak protection fortifying user anonymity and safeguarding against potential data leaks.
Private Internet Access VPN

Features: Private Internet Access VPN distinguishes itself with an expansive server network, facilitating access to geo-restricted content and optimizing connection speeds. The inclusion of an ad blocker and support for unlimited simultaneous connections further augments its appeal among users seeking a comprehensive VPN solution.
Security Standard: Embracing a robust security framework, Private Internet Access VPN integrates advanced encryption protocols and a strict no-logs policy, ensuring that user data remains confidential and inaccessible to external entities.
Safety: With an emphasis on safety, Private Internet Access VPN incorporates a kill switch mechanism and MACE technology, mitigating the risk of data leaks and bolstering user security while navigating the digital landscape.
Surfshark VPN

Features: Surfshark VPN captivates users with innovative features such as CleanWeb, which safeguards against malware and phishing attempts, and Multihop connections, enhancing user anonymity by routing traffic through multiple servers.
Security Standard: Surfshark VPN prioritizes user security, leveraging advanced encryption algorithms and a robust no-logs policy to create a very own secure network environment conducive to online privacy.
Safety: With safety at the forefront, Surfshark VPN offers features like a kill switch and camouflage mode, fortifying user anonymity and ensuring a secure browsing experience devoid of potential threats.
NordVPN

Features: NordVPN offers a multifaceted approach to online security, incorporating features like double VPN, which routes user traffic through two VPN servers, and dedicated IP addresses, enhancing user control and anonymity.
Security Standard: Exemplifying stringent security standards, NordVPN integrates advanced encryption protocols, dedicated IP options, and a comprehensive no-logs policy, fostering a secure and confidential online environment.
Safety: Prioritizing safety, NordVPN implements features such as CyberSec, which safeguards against intrusive ads and malicious websites, and a kill switch mechanism, ensuring uninterrupted protection against potential data leaks.
ExpressVPN

Features: ExpressVPN captivates users with an intuitive interface, optimized servers for streaming services, and impeccable connection speeds, ensuring a seamless browsing experience for users seeking unrestricted access to digital content.
Security Standard: ExpressVPN upholds rigorous security standards, employing advanced encryption protocols, TrustedServer technology, and a comprehensive no-logs policy to safeguard user data and preserve online privacy.
Safety: In terms of safety, ExpressVPN incorporates a kill switch mechanism, DNS leak protection, and split tunneling capabilities, fortifying user security and ensuring a secure browsing experience across various devices.
Key Features to Consider When Choosing a VPN
Choosing the right VPN requires careful evaluation of various factors. Here are some key features that you should consider when selecting a VPN:
Speed and Performance
A slow VPN can significantly hinder your online experience. Look for a VPN provider that offers high-speed connections and has servers located in close proximity to your region. Additionally, consider providers that offer features like split tunneling, which allows you to route specific traffic through a VPN while accessing other websites directly.
When it comes to speed and performance, it’s important to understand how a VPN works. A VPN creates a secure and encrypted connection between your device and the server you are connected to. This encryption process can sometimes slow down your internet speed, so it’s crucial to choose a VPN provider that has optimized their servers for fast and efficient performance.
Furthermore, some VPN providers offer advanced features like bandwidth throttling prevention, which ensures that your internet speed remains stable and unaffected even during peak usage hours. This can be particularly useful if you engage in activities that require a high-speed internet connection, such as streaming or online gaming.
Server Locations and Numbers
The number of server locations and their distribution throughout tor network is an essential factor to consider. A larger network of servers ensures better performance and the ability to bypass geo-restrictions more effectively.
When a VPN provider has servers in multiple locations, it allows you to connect to a server in a specific country or region, giving you access to content and services that may be restricted in your location. For example, if you want to access streaming platforms that are only available in the United States, having a VPN with servers in the US will allow you to bypass those restrictions and enjoy the content.
Furthermore, having servers in various locations also improves the overall speed and stability of your connection. When you connect to a server closer to your physical location, the distance your data needs to travel is reduced, resulting in faster speeds and lower latency.
Consider VPN providers that have a number of servers in the locations you frequently access or are interested in. Whether it’s for work, entertainment, or accessing content from different regions, having a wide range of server locations can greatly enhance your VPN experience.
Security Features and Protocols
Strong Encryption Standards: AES-256 and Beyond
In the realm of cybersecurity, encryption stands as a formidable shield against potential threats. When choosing the right VPN, it’s paramount to prioritize providers that implement robust encryption standards, such as AES-256. This encryption algorithm, renowned for its efficacy and resilience, ensures that your data remains cloaked in impenetrable layers of security.
The Advanced Encryption Standard (AES) with a 256-bit key length epitomizes the pinnacle of encryption technology. It leverages a complex mathematical formula to encrypt data, transforming it into an unintelligible format for unauthorized entities. This level of encryption not only safeguards your browsing data but also fortifies your online privacy, ensuring that your internet service provider or any malicious actors cannot decipher your activities.
Kill Switch Functionality: Preventing Data Leaks
In the intricate tapestry of VPN features, the kill switch functionality emerges as a crucial safeguard against potential data leaks. This security feature operates as a fail-safe mechanism, severing your internet connection if the VPN connection drops unexpectedly. By doing so, it prevents your web traffic from reverting to an unencrypted state, thereby preserving your online security and privacy.
Imagine a scenario where your VPN connection experiences intermittent disruptions. Without a kill switch, your device would revert to its standard internet connection, exposing your browsing data to potential surveillance or cyber threats. However, with the kill switch activated, such vulnerabilities are swiftly mitigated, ensuring a consistent shield of protection for your online activities.
DNS Leak Protection: Maintaining Anonymity
Navigating the labyrinthine corridors of the internet necessitates maintaining a veil of anonymity. DNS leak protection emerges as a pivotal feature in preserving your virtual privacy. Essentially, DNS leak protection safeguards against inadvertent exposure of your browsing data by ensuring that DNS queries are routed through the VPN server rather than your internet service provider’s DNS servers.
By channeling DNS queries through the encrypted tunnel of the VPN connection, DNS leak protection mitigates the risk of exposing your browsing history, IP address, and other sensitive information. It ensures that your virtual location remains concealed and that your online activities are indistinguishable, thereby fostering a sanctuary of anonymity amidst the bustling digital landscape.
Split Tunneling: Routing Select Traffic Through VPN
In the multifaceted domain of VPN functionalities, split tunneling emerges as a sophisticated feature, enabling users to delineate specific traffic to be routed through the VPN connection. This nuanced capability offers unparalleled flexibility, allowing you to selectively channel traffic based on your requirements.
For instance, you may opt to route streaming services or specific applications through the VPN tunnel while directing other traffic through your standard internet connection. This granular control empowers users to optimize connection speeds for specific tasks while simultaneously benefiting from the security features of the VPN service.
Free vs. Paid VPNs

While free VPNs may seem appealing, it’s important to understand their limitations and potential drawbacks. Let’s explore the pros and cons of both free and paid VPN options.
Pros and Cons of Free VPNs
Free VPNs can be enticing due to their zero-cost nature. However, they often come with limitations, such as restricted bandwidth, slower speeds, and a limited number of server locations. This means that when using a free VPN, you may experience slower internet speeds and may not be able to access certain websites or streaming platforms due to the limited server locations available.
Moreover, free VPNs may compromise your privacy online, by selling your data to third parties or displaying intrusive advertisements. When you use a free VPN, your online activities and personal information may be collected and sold to advertisers or other companies, compromising your privacy and potentially exposing you to targeted ads or even identity theft.
Another drawback of free VPNs is that they often have a limited number of simultaneous connections. This means that if you want to use the VPN on multiple devices, such as your smartphone, laptop, and tablet, you may not be able to do so simultaneously with a free VPN. This can be inconvenient if you have multiple devices that you want to protect with a VPN.
Advantages of Paid VPNs
Investing in a paid VPN provides numerous advantages that outweigh the limitations of free alternatives. Paid VPNs typically offer faster speeds, a larger server network, and stronger security features. With a paid VPN, you can enjoy faster internet speeds, allowing you to stream content, download files, and browse the web without any noticeable lag or buffering.
In addition, paid VPNs usually have a larger server network, giving you more options when it comes to choosing a server location. This can be beneficial if you want to access geo-restricted content or bypass censorship in certain countries. With a paid VPN, you can connect to servers in different countries and enjoy unrestricted access to websites and online services.
Most importantly, paid VPNs prioritize user privacy by adhering to robust privacy policies and offering reliable customer support. When you use a paid VPN, you can have peace of mind knowing that your online activities are not being logged or sold to third parties. Paid VPN providers often have strict no-logs policies, meaning that they do not keep any records of your online activities.
Furthermore, paid VPNs usually offer dedicated customer support to assist you with any issues or questions you may have. Whether it’s troubleshooting connection problems or seeking advice on optimizing your VPN settings, you can rely on the support team of a paid VPN to provide prompt and helpful assistance.
Setting Up and Using Your VPN

Step-by-Step Installation Guides
Embarking on the journey of choosing the right VPN can seem intricate, but the installation process need not be. Most VPN providers furnish user-friendly interfaces coupled with intuitive setup wizards, facilitating a smooth installation process even for novices.
- Selecting a VPN Provider: Begin by identifying a reputable VPN service provider that aligns with your security and privacy requirements. Evaluate factors such as server locations, connection speeds, and security features to make an informed decision.
- Downloading VPN Software: Navigate to the official website of your chosen VPN provider and download the appropriate software for your device’s operating system. Follow the on-screen prompts to initiate the installation process.
- Configuring Initial Settings: Once the VPN software is installed, launch the application and proceed to configure your preferred settings, including server locations and connection protocols. Some advanced features, such as split tunneling or double VPN, may require additional configuration.
- Activating the VPN Connection: Upon successful configuration, activate the VPN connection by selecting a server location of your choice. Your internet traffic will now be encrypted, and your IP address masked, ensuring enhanced online privacy and security.
Configuring VPN Settings for Optimal Security
Configuring your VPN settings judiciously is pivotal in maximizing both security and performance. Here’s how you can optimize your VPN and connection speed:
- Choosing the Right Protocol: Opt for VPN protocols that prioritize security, such as OpenVPN or WireGuard. These protocols employ robust encryption algorithms, safeguarding your browsing data from potential threats.
- Enabling Kill Switch: Activate the kill switch feature within your VPN software to ensure that your internet traffic remains encrypted even if the VPN connection drops unexpectedly, mitigating the risk of data leaks.
- Selecting Server Locations: Strategically select server locations that align with your browsing requirements. For instance, if you intend to access geo-restricted streaming services, choose a server located in the desired region.
- Customizing Connection Settings: Explore advanced features like split tunneling or dedicated IP options, tailoring your VPN connection to suit specific tasks or applications.
Tips for Troubleshooting Common Issues
Encountering technical glitches is an inevitable aspect of using any software, and VPNs are no exception. Here are some troubleshooting tips to address common VPN issues:
- Connection Drops: If your VPN connection drops intermittently, try switching to a different server location or protocol. Additionally, ensure that your VPN software is updated to the latest version.
- Slow Connection Speeds: If you experience sluggish internet speeds while using a VPN, try connecting to a server closer to your physical location. Alternatively, contact your VPN provider’s support team for assistance in optimizing connection speeds.
- Compatibility Issues: Ensure that your device’s operating system is compatible with the VPN software. If compatibility issues persist, consider reaching out to your VPN provider for tailored solutions.
Regularly Updating Your VPN Software

Staying abreast of the latest software updates is imperative in maintaining optimal security and performance. VPN providers frequently release updates encompassing security patches, performance enhancements, and new features.
Regularly check for updates within your VPN software and promptly install any available updates. By doing so, you ensure that your VPN software remains fortified against emerging threats, and you benefit from the latest advancements in online security and privacy.
Potential Drawbacks and Limitations
The utilization of Virtual Private Networks (VPNs) has proliferated in recent years, heralded for their prowess in enhancing online security and privacy. However, a nuanced exploration reveals potential drawbacks and limitations inherent in VPN technology. This article elucidates these challenges, encompassing performance issues, legal considerations, and strategies to overcome detection mechanisms.
Performance Issues: Impact on Speed and Latency
Bandwidth Limitations
While VPNs confer myriad benefits, they are not devoid of limitations, most notably, the potential degradation of connection speeds. The encapsulation of data within an encrypted tunnel necessitates additional processing overhead, which may culminate in reduced bandwidth and increased latency. Consequently, users may perceive a tangible decrement in download and upload speeds, particularly when connecting to distant VPN servers.
Server Congestion
The allure of VPN services often results in server congestion, especially among popular VPN providers offering limited server locations. This congestion can exacerbate performance issues, manifesting as unreliable connections and diminished connection speeds during peak usage hours.
Overhead Encryption
The encryption protocols employed by VPNs, while pivotal for ensuring data security, introduce computational overhead, thereby impinging upon the overall performance of the internet connection. The confluence of encryption algorithms and data encapsulation processes may precipitate latency spikes, particularly on networks with constrained computational resources.
Legal Considerations: VPN Usage in Various Countries
Regulatory Restrictions
The proliferation of VPN usage has elicited regulatory scrutiny in various jurisdictions, leading to the imposition of restrictions and prohibitions on VPN usage. Countries such as China and Russia have implemented stringent regulations, compelling VPN providers to adhere to state-mandated guidelines and facilitate governmental surveillance efforts.
Ambiguous Legal Landscape
The legal landscape governing VPN usage remains nebulous and subject to evolving interpretations, engendering uncertainty and apprehension among users and VPN providers alike. The absence of standardized regulations across jurisdictions complicates compliance efforts and fosters a climate of ambiguity surrounding VPN usage.
Jurisdictional Concerns
The jurisdiction in which a VPN provider operates is paramount, as it delineates the legal framework governing data retention policies, government surveillance mandates, and user privacy rights. Users must scrutinize the jurisdictional affiliations of VPN providers and ascertain the implications for their data privacy and security.
Overcoming Blocks: VPN Detection and Countermeasures
Evasion Techniques
The detection of VPN usage by streaming services and online platforms has precipitated the development of evasion techniques, including obfuscation protocols and stealth VPN technologies. These mechanisms endeavor to circumvent VPN detection mechanisms by emulating standard internet traffic patterns, thereby preserving access to geo-restricted content.
Dynamic Server Switching
Dynamic server switching represents a stratagem employed by VPN users to evade detection mechanisms and mitigate the risk of IP address blacklisting. By periodically switching between VPN servers and employing load balancing techniques, users can obfuscate their digital footprint and mitigate the risk of detection.
Protocol Diversification
The diversification of VPN protocols, encompassing OpenVPN, L2TP/IPsec, and IKEv2/IPsec, among others, facilitates evasion of detection mechanisms by leveraging disparate encryption algorithms and encapsulation techniques. By alternating between protocols, users can obfuscate their VPN usage patterns and enhance their resilience against detection mechanisms.
Evaluating VPN Providers

Reputation and User Reviews
In the digital age, where online privacy and security have become paramount concerns, the role of a Virtual Private Network (VPN) cannot be overstated. However, with a plethora of VPN providers flooding the market, choosing the right VPN service can be a daunting task.
One of the primary metrics to consider is the reputation of the VPN provider. A quick scan through user reviews and testimonials can provide invaluable insights into the reliability and performance of the service. Delve deeper into forums and online communities where VPN users share their experiences, emphasizing factors such as connection speeds, server reliability, and customer support.
Moreover, reputable VPN companies often prioritize transparency, showcasing their security features, server networks, and privacy policies prominently on their websites. A provider that adheres to a strict no-logs policy ensures that your browsing data remains confidential, further bolstering its credibility in the market.
Customer Support and Service
Beyond the technical aspects, the quality of customer support offered by a VPN service provider plays a pivotal role in enhancing user experience and satisfaction. Robust customer support ensures that any queries or issues related to the VPN connection are promptly addressed, minimizing downtime and ensuring a seamless browsing experience.
Look for VPN providers that offer multiple channels of communication, including live chat support, email assistance, and comprehensive knowledge bases. A responsive support team can significantly alleviate concerns regarding connection drops, slow speeds, or any other technical hitches that may arise during VPN use.
Additionally, consider VPN companies that provide a dedicated IP option, allowing for more reliable and secure remote access. The availability of a kill switch feature is another crucial aspect to evaluate, as it ensures that your internet traffic remains encrypted even if the VPN connection drops unexpectedly.
In conclusion, the process of selecting the best VPN service involves a meticulous evaluation of various factors, ranging from reputation and user reviews to customer support and service quality. Prioritize VPN providers with a proven track record of reliability, robust security features, and responsive customer support.
By conducting thorough research and leveraging user feedback, you can make an informed decision, ensuring that your online privacy and security are uncompromised. Remember, the right VPN not only encrypts your web traffic and shields your IP address but also provides a reliable connection and seamless browsing experience, enabling you to navigate the digital realm with confidence and peace of mind.
Choosing the right VPN is not a decision to be taken lightly. By understanding the basics of VPNs, grasping their importance, and considering the key features and attributes of VPN providers, you can ensure that you select a VPN that meets your needs and safeguards your online privacy and security. Remember, a VPN is your digital shield in the vast and ever-evolving online world. Stay safe and protected with the right VPN by your side.

