Protecting our personal information has become more crucial than ever. With cyber threats and data breaches on the rise, it is important to understand the basics of data encryption and how it can keep your information secure. So, let’s dive into the world of data encryption and explore its different types, the encryption process, standards and protocols, and how you can implement it effectively.
Understanding the Basics of Data Encryption

In today’s digital age, where information is constantly being transmitted and stored, it is crucial to ensure the security and confidentiality of sensitive data. One of the most effective ways to achieve this is through data encryption software. Data encryption is the process of converting your information into an unreadable format to prevent unauthorized access.
When you encrypt your data, you are essentially scrambling it using complex algorithms and transforming it into ciphertext. This ciphertext can only be deciphered with the right decryption key, which acts as the secret code to unlock the encrypted data.
What is Data Encryption?
Data encryption is the practice of encoding data to protect its confidentiality. It is a process that involves transforming plaintext, which is the original readable form of the data, into ciphertext, which is the encrypted and unreadable form of the data. This transformation is achieved through the use of cryptographic algorithms, which are complex mathematical formulas designed to scramble the data in a way that is virtually impossible to reverse without the correct decryption key.
When data is encrypted, it becomes extremely difficult for unauthorized individuals to access or understand the information. Even if they manage to intercept the encrypted data, they would need the decryption key to make any sense of it. This makes data encryption an essential tool in protecting sensitive information, to protect data such as personal details, financial records, and confidential business data.
The Importance of Data Encryption
With the increase in cyber attacks and data breaches, data encryption has become an essential part of safeguarding sensitive information. It is no longer enough to rely solely on firewalls and other security measures to protect your data. Encrypting your data adds an extra layer of security, making it significantly more challenging for hackers and cybercriminals to gain access to your information.
This ensures that the data remains intact and trustworthy, as any unauthorized changes will be immediately apparent when attempting to decrypt the unencrypted data.
Furthermore, data encryption is not limited to data at rest, such as files stored on a computer or a server. It also applies to data in transit, such as information being transmitted over the internet. Encrypting data during transmission ensures that even if it is intercepted by hackers, they will only see a jumble of meaningless characters, making it impossible for them to extract any valuable information.
Data encryption is a critical component of modern-day security practices. It provides a robust defense against unauthorized access, ensuring the confidentiality, integrity, and authenticity of sensitive information.
Different Types of Data Encryption
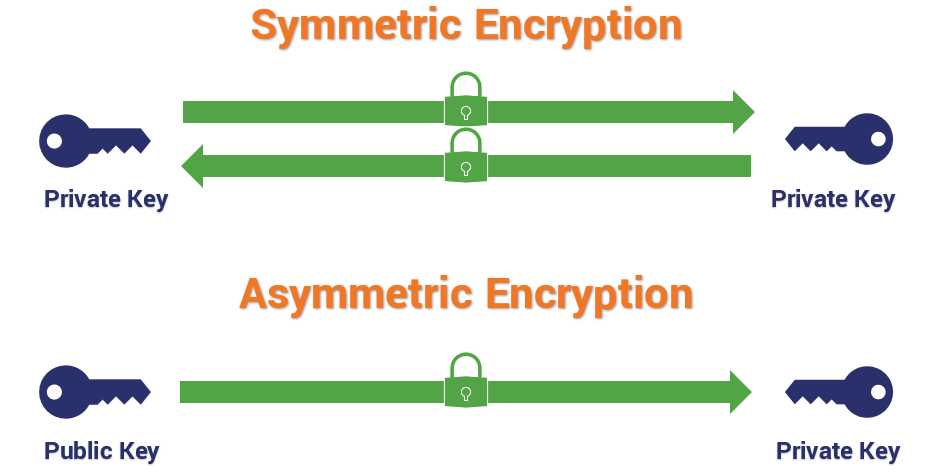
When it comes to protecting sensitive information, data encryption software plays a crucial role. There are different types of data encryption that offer varying levels of security. The two main types are symmetric encryption and asymmetric encryption.
Data encryption is the process of converting plain text into cipher text, making it unreadable to unauthorized individuals. Let’s explore these two types of data encryption algorithms in more detail.
Symmetric Encryption
Symmetric encryption, also known as secret-key encryption, is a widely used method for securing data. It uses the same key for both encryption and decryption. This means that the sender and the recipient must have access to the same secret key.
One of the advantages of symmetric encryption is its speed and efficiency. It can encrypt and decrypt large amounts of data quickly, making it ideal for applications that require high-speed processing. However, the challenge lies in securely sharing the encryption key with the intended recipient.
To address this challenge, various cryptographic key exchange algorithms and protocols have been developed. These mechanisms ensure that the encryption key is securely transmitted between the sender and the recipient, minimizing the risk of interception or unauthorized access.
Additionally, symmetric encryption algorithms come in different strengths and complexities. Advanced Encryption Standard (AES) is one of the most widely used symmetric encryption algorithms, offering a high level of security.
Asymmetric Encryption
Asymmetric encryption, also known as public-key encryption, is another popular method for securing data. Unlike symmetric encryption, asymmetric encryption uses two different keys: a public key to encrypt the data and a private key to decrypt it.
This type of encryption eliminates the need for securely sharing a single key, as each user has a unique private key encryption and pair. The public key can be freely distributed, while the private key is kept secret and known only to the owner. This enables secure communication between parties without the risk of key interception.
However, asymmetric encryption is slower and computationally more intensive than symmetric encryption. The encryption and decryption processes involve complex mathematical computations, which can impact performance in resource-constrained environments.
Despite its computational overhead, asymmetric encryption offers additional security benefits. It enables digital signatures, which verify the authenticity and integrity of data, and facilitates secure key exchange protocols, such as the Diffie-Hellman key exchange algorithm.
Popular asymmetric encryption algorithms include RSA (Rivest-Shamir-Adleman) and Elliptic Curve Cryptography (ECC). These algorithms provide different levels of security and are widely used in various applications, including secure communication protocols and digital certificates.
Overall, both symmetric and asymmetric encryption play crucial roles in securing sensitive data. The choice between the two depends on the specific requirements of the application, balancing factors such as speed, security, and key management.
The Process of Data Encryption
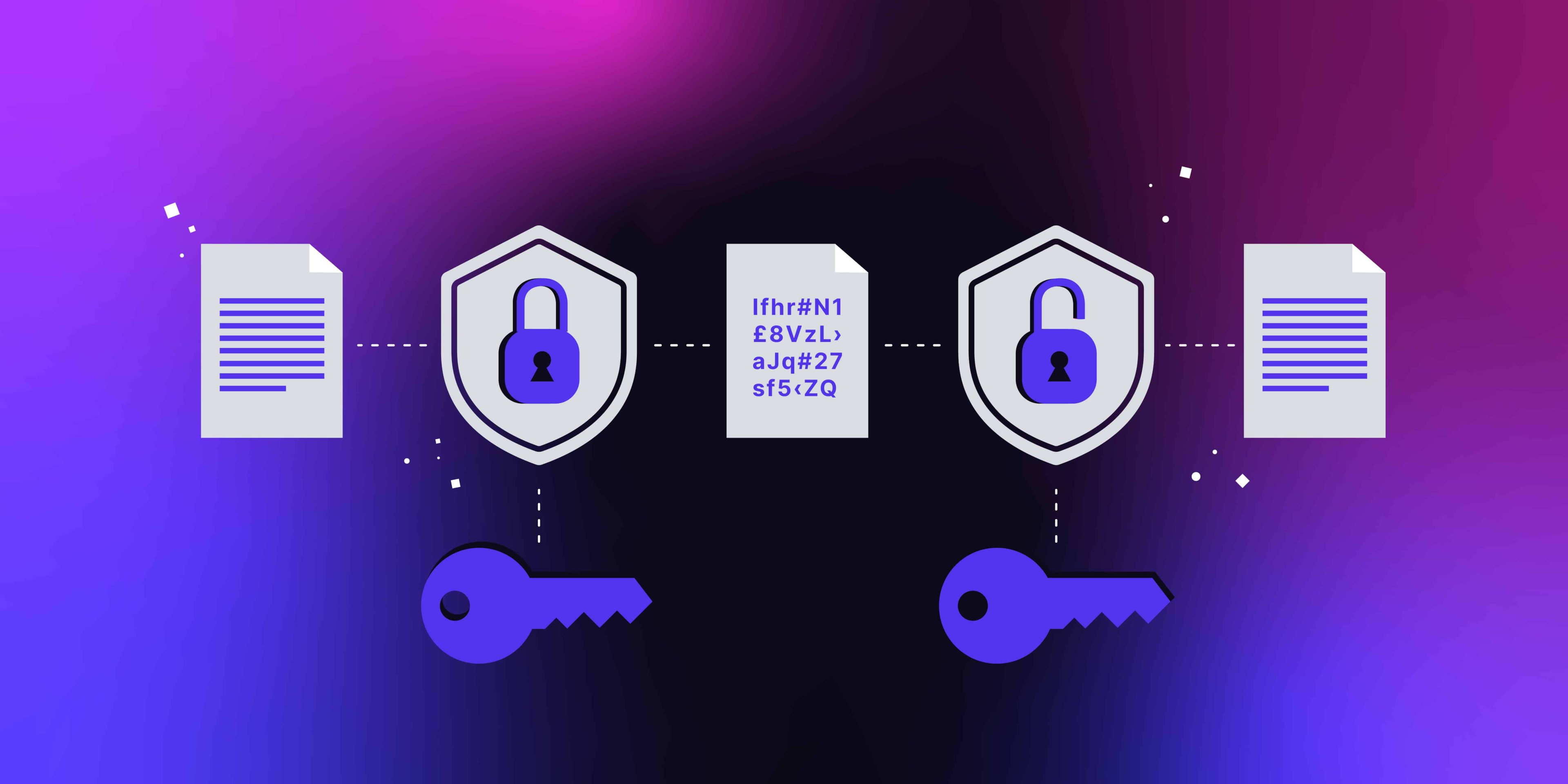
Now that we understand the basics and types of data encryption, let’s take a closer look at how data encryption works and the importance of key management.
Data encryption is a complex process that involves several steps to ensure the security and confidentiality of sensitive information. The encryption process begins by breaking down the data into small blocks, which are then encrypted using a specific encryption algorithm and an encryption key.
The encryption algorithm is a mathematical formula that transforms the plaintext data into an unreadable form, known as ciphertext. This transformation ensures that even if an unauthorized person gains access to the ciphertext, they will not be able to understand or make sense of the information without the decryption key.
The encryption key is a unique string of characters that is used to encrypt and decrypt the data. It is essential to keep the encryption key secure and confidential to prevent unauthorized access to the encrypted information. Without the correct encryption key, it is virtually impossible to decrypt the ciphertext and retrieve the original plaintext.
Once the data is encrypted and transformed into ciphertext, it can be transmitted or stored securely. During transmission, the ciphertext is sent over a secure channel, such as a virtual private network (VPN) or a secure socket layer (SSL), to ensure that it cannot be intercepted or tampered with by unauthorized individuals.
To decrypt the data, the recipient uses the corresponding decryption key and algorithm to reverse the encryption process. The decryption key is a unique string of characters that is mathematically related to the encryption key. It allows the recipient to transform the ciphertext back into the original plaintext, making it readable and understandable.
Key Management in Data Encryption
Key management is a critical aspect of data encryption that ensures the security and integrity of the encryption process. It involves securely generating, storing, distributing, and revoking encryption keys.
Generating encryption keys involves using a random number generator or a cryptographic algorithm to create unique and unpredictable keys. The keys must be generated in a secure environment to prevent any potential compromise or unauthorized access.
Storing your own encryption software and keys requires careful consideration to prevent unauthorized access or loss. Encryption keys should be stored in a secure location, such as a hardware security module (HSM) or a key management system (KMS), that provides strong physical and logical protection.
Distributing encryption keys to authorized parties is a delicate process that requires secure channels and protocols. It is crucial to ensure that only the intended recipients receive the encryption keys and that they are not intercepted or tampered with during transmission.
Revoking encryption keys is necessary when a key is compromised or when access to encrypt sensitive data needs to be revoked for security reasons. Key revocation ensures that unauthorized individuals cannot decrypt the ciphertext and gain access to the sensitive information.
Effective key management is essential to maintain the security and confidentiality of encrypted data. It minimizes the risk of key compromise and ensures that only authorized parties have access to the decryption keys for computer systems.
Practical Tips for Individuals: Enhancing Data Security
Encrypting Personal Devices: Laptops, Smartphones, and Tablets
In an era where sensitive data plays a pivotal role in our daily lives, encrypting personal devices is a fundamental step towards safeguarding information. Data encryption is a powerful shield, rendering unauthorized access to confidential data nearly impossible. Implementing advanced encryption standards, such as the Triple Data Encryption Standard (3DES) or the Advanced Encryption Standard (AES), ensures that your data remains impenetrable.
When you encrypt data on your laptop, smartphone, or tablet, you essentially convert it into an unreadable format, making it indecipherable without the correct encryption key. The encryption key acts as a secret code, and it is crucial to keep it secure. Modern encryption algorithms, including asymmetric encryption methods, add an extra layer of protection, using both a public key for encryption and a private key for decryption.
Encrypting data at rest, whether it’s stored on your device’s hard drive or in cloud storage, guarantees that even if your device falls into the wrong hands, the information remains inaccessible. Full disk encryption is a robust solution, ensuring that every bit of data stored on your device is protected.
Secure Browsing: Using VPNs and HTTPS
When it comes to online security, securing your browsing activities is paramount. Utilizing a Virtual Private Network (VPN) ensures that data in transit is encrypted, shielding it from potential eavesdroppers. VPNs employ symmetric and asymmetric encryption methods, making it challenging for unauthorized users to intercept or decipher your transmitted data.
Additionally, always opt for websites using HTTPS (Hypertext Transfer Protocol Secure). This cryptographic protocol encrypts data during its transit, enhancing the security of information exchanged between your device and the website’s server. Public key cryptography, which underlies HTTPS, involves both a public key for encryption and a private key for decryption, providing a secure channel for your online interactions.
Password Management: Creating Strong and Unique Passwords
The cornerstone of digital security lies in creating strong and unique passwords. Employing a combination of uppercase and lowercase letters, numbers, and special characters fortifies your passwords against various cyber threats. Avoid common phrases or easily guessable information, opting instead for a unique sequence that only you could decipher.
Consider using a reputable password manager to generate and store complex passwords securely. These tools not only simplify the process of creating strong passwords but also alleviate the burden of remembering them. Regularly updating passwords and refraining from using the same password across multiple accounts further fortifies your digital fortress.
Two-Factor Authentication: Adding an Extra Layer of Security
Two-factor authentication (2FA) serves as an additional barrier, fortifying your digital presence by requiring more than just a password for access. This multi-layered approach typically combines something you know (password) with something you have (a temporary code sent to your mobile device). In essence, even if your password is compromised, unauthorized access remains improbable without the secondary authentication factor.
Enabling 2FA across your accounts, especially for critical platforms like email, banking, and social media, adds a robust layer of defense against potential data theft. This method ensures that even if someone gains access to your password, they would still require the temporary code, which constantly changes, to breach your account.
Data Encryption Standards and Protocols
To ensure interoperability and compatibility, various standards and protocols govern the implementation of data encryption systems. Understanding these standards is essential in selecting the appropriate encryption solution.
Data encryption is a fundamental aspect of information security. It involves transforming data into an unreadable format, known as ciphertext, to protect it from unauthorized access. Encryption standards and protocols play a crucial role in ensuring the confidentiality, integrity, and authenticity of sensitive information.
Common Data Encryption Standards
Data Encryption Standard (DES), Advanced Encryption Standard (AES), and Triple Data Encryption Standard (3DES) are some of the most widely used encryption standards. These standards define the encryption algorithms and key lengths used to protect sensitive information.
The Data Encryption Standard (DES) was developed in the 1970s and became the most widely used encryption algorithm for several decades. However, due to advances in computing power, DES is no longer considered secure enough for modern applications. As a result, the Advanced Encryption Standard (AES) was introduced in 2001 as a replacement for DES. AES is a symmetric encryption algorithm that uses a variable key length, making it more secure against brute-force attacks.
Triple Data Encryption Standard (3DES), also known as TDEA or Triple DES, is a symmetric encryption algorithm that applies the DES algorithm three times to each data block. This provides a higher level of security compared to DES, making it suitable for applications that require stronger encryption.
Understanding Encryption Protocols
Encryption protocols, such as Secure Sockets Layer (SSL) and Transport Layer Security (TLS), are used to facilitate secure communication over networks. These protocols establish encrypted connections and provide authentication, encryption protects data integrity, and confidentiality.
Secure Sockets Layer (SSL) was developed by Netscape in the 1990s to secure online transactions. It has since been replaced by Transport Layer Security (TLS), which is an updated version of SSL. TLS is widely used to secure web communication, including online banking, e-commerce, and email services.
TLS operates at the transport layer of the network protocol stack and ensures that data exchanged between client and server remains confidential and tamper-proof. It uses a combination of symmetric and asymmetric encryption algorithms to secure data transmission and establish a secure connection. The client and server negotiate a mutually supported encryption algorithm and exchange cryptographic keys to encrypt and decrypt data.
Encryption protocols like SSL and TLS provide a secure channel for data transmission, protecting sensitive information from eavesdropping and tampering. They also verify the authenticity of the communicating parties, preventing man-in-the-middle attacks.
The data encryption standards and protocols are essential components of modern information security. They enable organizations to protect sensitive data from unauthorized access and ensure secure communication over networks. Understanding these standards and protocols is crucial for selecting and implementing effective data encryption solutions.
Implementing Data Encryption
Implementing data encryption requires careful consideration of various factors to ensure it aligns with your specific needs and offers optimal data protection, for your information.
Data encryption security
Implementing encryption effectively involves following best practices such as regularly updating encryption algorithms, monitoring encryption processes, and conducting periodic security audits. Additionally, user education and awareness play a vital role in maintaining a secure data encryption environment.
Data encryption is a fundamental concept in keeping your information secure. Understanding the basics of file encryption, different types, and the encryption process can help you make informed decisions regarding the protection of your data. By implementing the right encryption solution and following best practices, you can safeguard your sensitive information and mitigate the risks posed by cyber threats and data breaches.

